You are here
A Deep Learning based Approach for Intrusion Detection System - GitHub - sss/Master-thesis: A Deep Learning based Approach for Intrusion Detection System Therefore, SVM is applied in intrusion detection, it can overcome the defects of intrusion detection method commonly and achieve good detection blogger.come of the highly regularity of the network protocol of the data package, a new intrusion detection method is suggested, in order to improve the efficiency Master Thesis: Title: Intrusion Detection System Framework for Internet of Things: Authors: Becker, Johan Vester, My: Abstract: Today, we see an increasing trend towards connected devices. This trend of connecting devices instead of people is called the Internet of Things (IoT)
Feedback and support
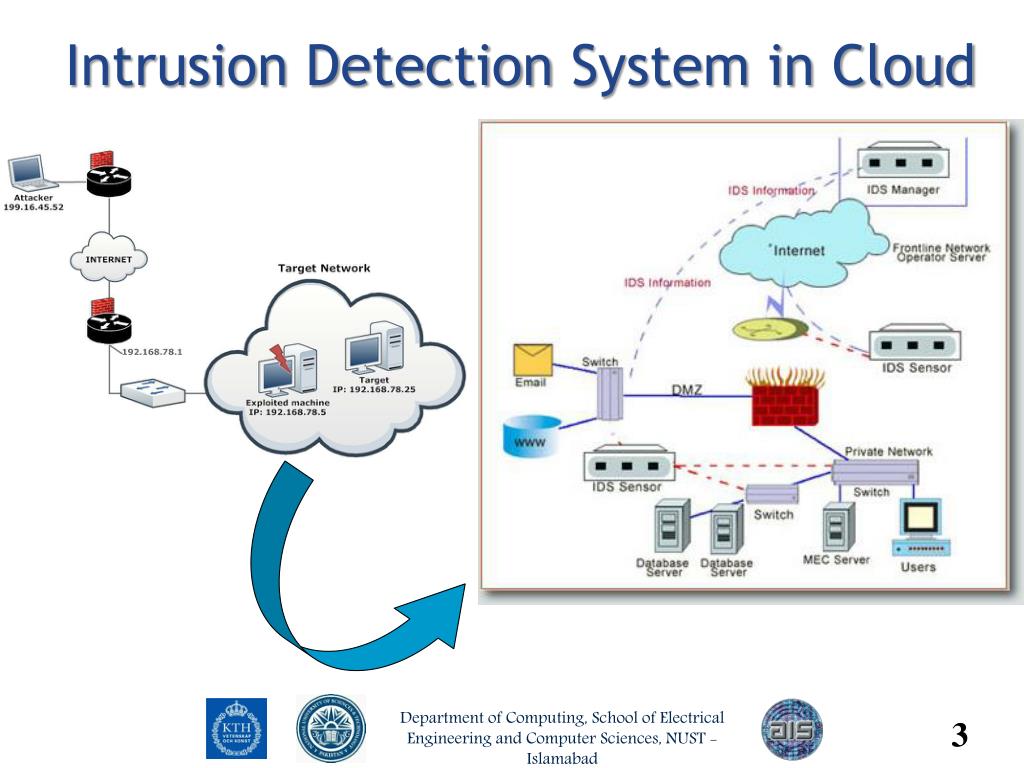
An Intrusion Detection System (IDS) is the tool, software or hardware, that allows the auto- mated detection of intrusions inside a monitored network, while the same tool is called Intrusion Prevention System (IPS) in case it also automates the counter- measures against these intrusions Master’s Thesis Intrusion detection for grid and cloud computing By Vamsi Krishna Popuri LiTH-ISY-EX/SE Examiner & Supervisor Dr Viiveke Fåk Linköping Institute of Technology. 4. Presentation Date Publishing Date (Electronic version) Need for Intrusion Detection System 2 Terminologies 2 Risk 2 Vulnerability 2 Attack 3 Penetration 3 Classification of IDS 3 Intrusion Detection Techniques 3 Anomaly Detection 3 Misuse detection 4 IDS Data sources 5 Host-based IDS 5 Network-based IDS 6
About this service
This thesis targets security analysis for IoT, where the analysis should be spread out: the nodes, the edge, and the cloud. The goal is to design and evaluate a (future) intrusion detection systems that encompass all levels. During the thesis, you will (1) get familiar with existing analysis techniques, especially comparing local device Type: Master's thesis Year: Downloads: 10 Quote: 0 Intrusion detection based on machine learning has been a hot topic of network security research. Through getting information from training data, it establishes a detection model which is for distinguishing normal state from intrusion state Master Thesis: Title: Intrusion Detection System Framework for Internet of Things: Authors: Becker, Johan Vester, My: Abstract: Today, we see an increasing trend towards connected devices. This trend of connecting devices instead of people is called the Internet of Things (IoT)

You are here
Design and implementation of an intrusion detection system (IDS) for in-vehicle networks Master’s thesis in Computer Systems and Networks NORÄS SALMAN MARCO BRESCH Department of Computer Science and Engineering CHALMERSUNIVERSITY OFTECHNOLOGY UNIVERSITY OFGOTHENBURG Gothenburg, Sweden Master’s thesis i Master of Science in Technology Thesis Department of Computing, Faculty of Technology University of Turku Subject: Cyber Security Programme: Master’s Degree Programme in Information and Communication Technology Author: Donatus Ifeanyichukwu Edeh Title: Network Intrusion Detection System using Deep Learning Technique Number of pages: 75 pages, 2 techniques for intrusion detection are statistical methods, data mining methods [8], genetic algorithms, etc. [9]. The information presented in the thesis report is also presented in the paper, "A Survey of Intrusion Detection Techniques” (accepted by IEEE International Conference on Machine Learning Applications ) [10]

Latest commit
techniques for intrusion detection are statistical methods, data mining methods [8], genetic algorithms, etc. [9]. The information presented in the thesis report is also presented in the paper, "A Survey of Intrusion Detection Techniques” (accepted by IEEE International Conference on Machine Learning Applications ) [10] A Deep Learning based Approach for Intrusion Detection System - GitHub - sss/Master-thesis: A Deep Learning based Approach for Intrusion Detection System Master Thesis Utilizing the SHAP framework to bypass intrusion detection systems Author: Jonas Mossin Wagle Supervisor: ˜yvind Ytrehus June 1, Abstract The number of people connected to the internet is swiftly growing, and technology is
No comments:
Post a Comment